Hi!
Jens Müller presented in august 2020 some security issues in several popular PDF software. He did not test SumtraPDF. See here:
So maybe the authors could check if any of that applies to SumatraPDF.
Regards,
David

Hi!
Jens Müller presented in august 2020 some security issues in several popular PDF software. He did not test SumtraPDF. See here:
So maybe the authors could check if any of that applies to SumatraPDF.
Regards,
David

Occasionally SumatraPDF may be targeted to test some forms of PDF (PDF = Portable-Document-Flaws) and those may also include as per this study “vulnerabilities in all major PDF viewers.”
However, the difference (at this time) is that SumatraPDF with its LACK of under the hood popular and non-essential sophisticated features (often those driven by JavaScript) means it is usually safer / more immune to exploits. So in this case would not be expected to be affected.
The presentation included a broad range of known methods to leverage PDF’s
Denial-of-Service attacks affecting the host on which the document is processed.
Information disclosure attacks which track who opens a document or leak personal data out of the victim’s computer to the attacker’s server, such as PDF document form data, local files, or user credentials.
Data manipulation attacks which modify form values, write local files on the host system, or mask the displayed content of a document based on the opening application.
Execution of code on the victim’s machine, by silently launching an embedded executable.
In some of those attack vectors, SumatraPDF with its dependency on MuPDF could potentially be impacted, but generally without JavaScript enabled/involved, does not offer interactive form filling or other dynamic features such as signing / running embedments or other rich objects.
Whilst not listed I would expect SumatraPDF to share a similar result to MuPDF - (But without Scripting) and we can see MuPDF (Linux) shows up as most secure and if tested against that suite SumatraPDF should appear as the most secure.
For the DOS (infinite loop)
The test files targeted MuPDF on Linux, and so cause some similar problems for MuPDF-GL (Windows)
However SumatraPDF, refuses to run the 3 example file JavaScript contents and has no problems showing the raw page content without JavaScript empowered.
For the RCE example MuPDF-GL (with the windows test)
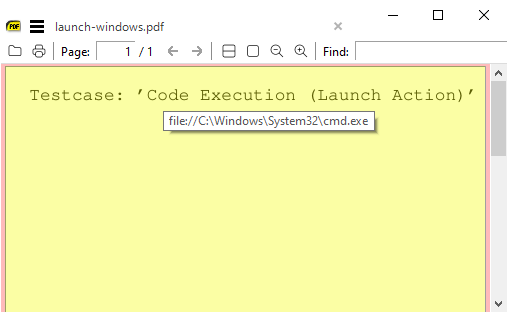
Testcase: ’Code Execution (Launch Action)’
Then both MuPDF and SumatraPDF block automatic running and Just like Acrobat when secured and others passing that test would require the user to confirm they want to run the executable code (thus are secured except from an exploitable user  )
)
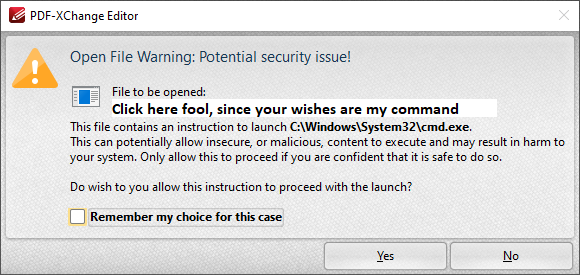
Also due to a current bug SumatraPDF accidentally protects a user from running any executable link even if they were foolish to attempt do so

In summary
Perhaps there was no need to compare / list SumatraPDF as there would (for that suite) be nothing to show.

“The Portable Document Format is insecure and dangerous!”
“For more details, please download the Presentation and White Paper PDFs.”



Jens Müller (the printer hacker) in 2018-god-mueller presentation describes themself as a “Passionate bounty hunter” and has published many similar Office Document Security and Privacy papers using both MS 365 generated PDF (containing users details) and PDF showing details of out of date versions of LaTeX.
Many topics are based around why printers are vulnerable and cannot be trusted as safe, with the end line “PostScript must die!”
And I must admit I too think as a format PDF / PS is insecure, and should be limited in what it is allowed to do, i.e as initially intended, it should confine itself to drawing objects on its canvas, and NO more than that.